Why abandoned domain names are dangerous for your business?
[08/03/2019]
Not renewing a domain name can compromise the security of a business, in particular, through the use of the associated email.
By buying six expired domain names which formerly belonged to legal practices, cybersecurity experts were able to retrieve 25 000 emails and enclosures, get access to approximately thirty legal professionals and social networks, as well as to PayPal accounts, Dropbox, G Suite or Office 365. How was this possible?

An unknown danger from the inside,
As for trademarks, managing a domain name portfolio does not imply that all domain names will be systematically renewed. The development of the business’s naming and of the services offered requires regular rationalization of the portfolio by abandoning certain domain names that are no longer intended to be used.
However, a domain name that has been registered leaves a “footprint” that is often ignored when not renewed.
A domain name that has not been renewed will fall into public domain. Thus, according to the “first-come, first-served principle”, anyone can reserve it. A bad actor can thus easily recreate the email addresses previously associated to this domain and get access to information related thereto (logins and emails).
Domain names are not just limited to a website
A domain name is still often only associated to a web use such as a website <www.mydomain.com>. And, the use of the email address <gael@mydomain.com> is also related to this domain name.
For third parties, domain names allow to identify you, this is especially true when using email. This can be regularly observed through scams to the president and other phishing attempts that use domain names which are very similar to legitimate domain names.
Above all, email addresses now play a crucial role for authentication on the internet: login to social networks, bank accounts, professional portals, online payments, e-commerce, taxes, etc.
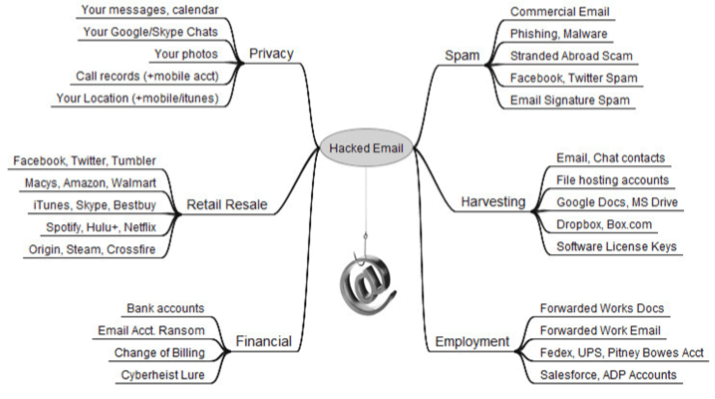
We are all aware of the danger of email address hacking. We should have the same awareness when abandoning a domain name associated with email addresses: the future holder can easily recreate these addresses.
There are also very simple technical solutions allowing to recover “on the fly” all the emails sent to a domain <* @ mydomain.com> without having to recreate the former addresses. A simple catch-all will do the job.
6 expired domain names, 25 000 emails retrieved and 30 employee accounts identified
Although this danger is not new, a proof of concept has recently been carried out by the cyber security expert, Gabor Szathmari, and his team.
Merger – acquisition…and abandoned domain names
On the basis of numerous mergers of Australian legal firms, Gabor Szathmari has noticed that many of them simply dropped their domain name in favour of the new merging entity.
It is very easy to analyse non-renewed and expiring domain names. Lists are available, and the watch can be carried out by thematic keyword to target a field of activity: legal, defence, nuclear, industry, etc.
Passive use of a domain name previously registered
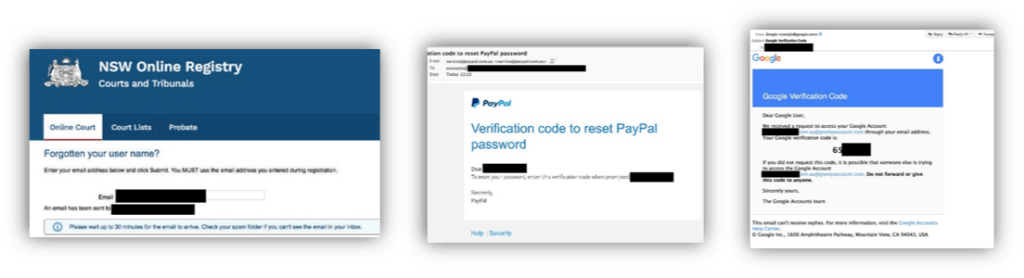
After identifying six abandoned domain names and proceeded to their reservation once those had fell into the public domain, the experts set up a catch-all to capture all emails sent to these domains.
First, they saw newsletters and then bank emails:
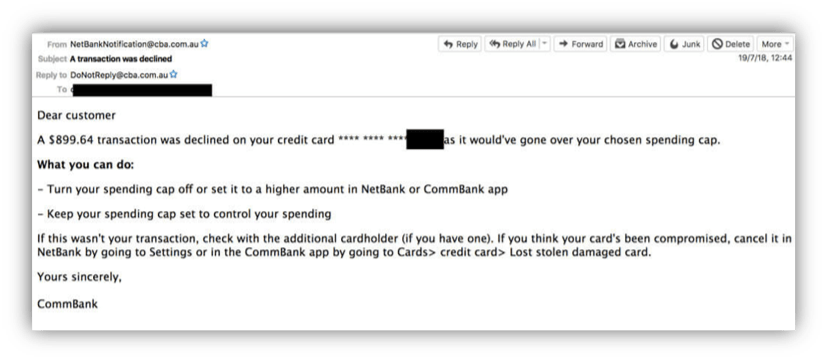
Then, emails from fellow-members and social network notifications …
Setting up a simple catch-all allows to both identify addresses that previously existed, and their different associations with online accounts (social networks, banks, etc.)..
Sensitive information was quickly retrieved, such as legal decisions, clients’ requests, agents’ fees and Uber trip data.
But, the researchers did not just passively sniff emails sent to the different domains, they also studied the different online accounts associated thereto.
Active use of a domain name previously registered
Various services now offer username / login monitoring and notifications in case of password leaks. These are very convenient, businesses can so monitor leaks of password and email combinations whose emails addresses are associated to their businesses. This monitoring is carried out on the “parent” domain name for example <* @ mycompany.com> and not directly and individually on each email address.
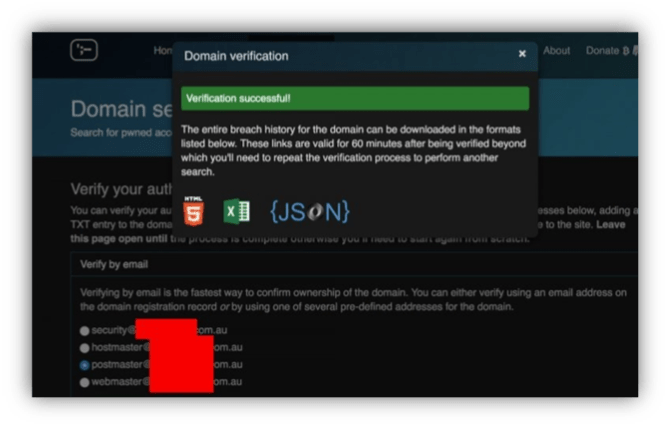
These services, for obvious security reasons, require the confirmation of the ownership of the domain name which you wish to monitor. Such verification has to be carried out by the domain holder. This posed no problem for the team of researchers that was able to authenticate these domains with Haveibeenpwned et SpyCloud in order to identify the corresponding email addresses.
Once the verification was complete, the user accounts associated to the domains and passwords were exposed.
In case of bad password practice (weak passwords used on several online services), it is possible to log in to user accounts of former staff, and to reset the password, if required.
The worst being that, the password reset allowed them to get access to professional portals such as services Paypal, Dropbox, Office 365 and G suite
The researchers did not complete the final step and just carried out a technical demonstration, this PoC demonstrates how vulnerable a business may be when not renewing a domain name. However, the conclusion could have been different if the researchers had been bad actors.
The possibilities offered with such practise are numerous:
- Hacking (compromise of access to various online resources, falsification / deletion of documents, access to online payment means)
- Extortion (request for change of bank account information with suppliers, customers and colleagues)
- Damage to reputation (leaks of sensitive data in an area covered by professional secrets)
- Economic intelligence (recovery of sensitive information, business secrets)
- Identity theft (fraud to the president)
- etc…
Above all, this practice has existed for years and continues to be made possible by domain abandonments that are not or poorly analysed. It is essential to implement good practises, when required.
How to protect yourself?
Preventively
In order to be protected from such attack, it is important:
- To identify the domains used for email within your domain name portfolio
- To have a strong password policy (with unique and complex passwords for each use)
- To implement two-factor authentication when possible
In case of domain name abandonment
- Identify the services associated to emails related to this domain
- Delete or update them if necessary
- Ensure that you are no longer identified by this domain by suppliers, clients, prospects: email information campaign, cleaning of web pages mentioning these emails
- Monitor your expired domain names! Keep a list of your current or past assets, and monitor any reactivation of any abandoned domain name.
Such as with your trademark portfolio, the rationalization of your domain name portfolio has to be studied in detail. Some domain names may be resold, while others are to be maintained.
If in doubt, first keep your domain name for a few years to set up redirections to your new domain. Then, you will be able to consider deactiving your former domain name (deletion of DNS servers) while being renewed, in order to indicate web or mail contacts in error (404 for the web, 512 or 550 for email).
Our firm may assist you in managing your trademark and domain name portfolio to ensure cohesion and maximize its potential. Please do not hesitate to contact us.
Source: the survey by Gabor Szathmari is available here.
The author :
Gaël Mancec | NTIC Attorney
Germain Maureau
gael.mancec@germainmaureau.com
+ 33 (0) 4 72 69 84 30
Download the .pdf version here : Usernamesv-en-pdf
